One Of The Best Tips About How To Detect Wireless Intrusion

(optional) to apply this action to all subfolders of your current.
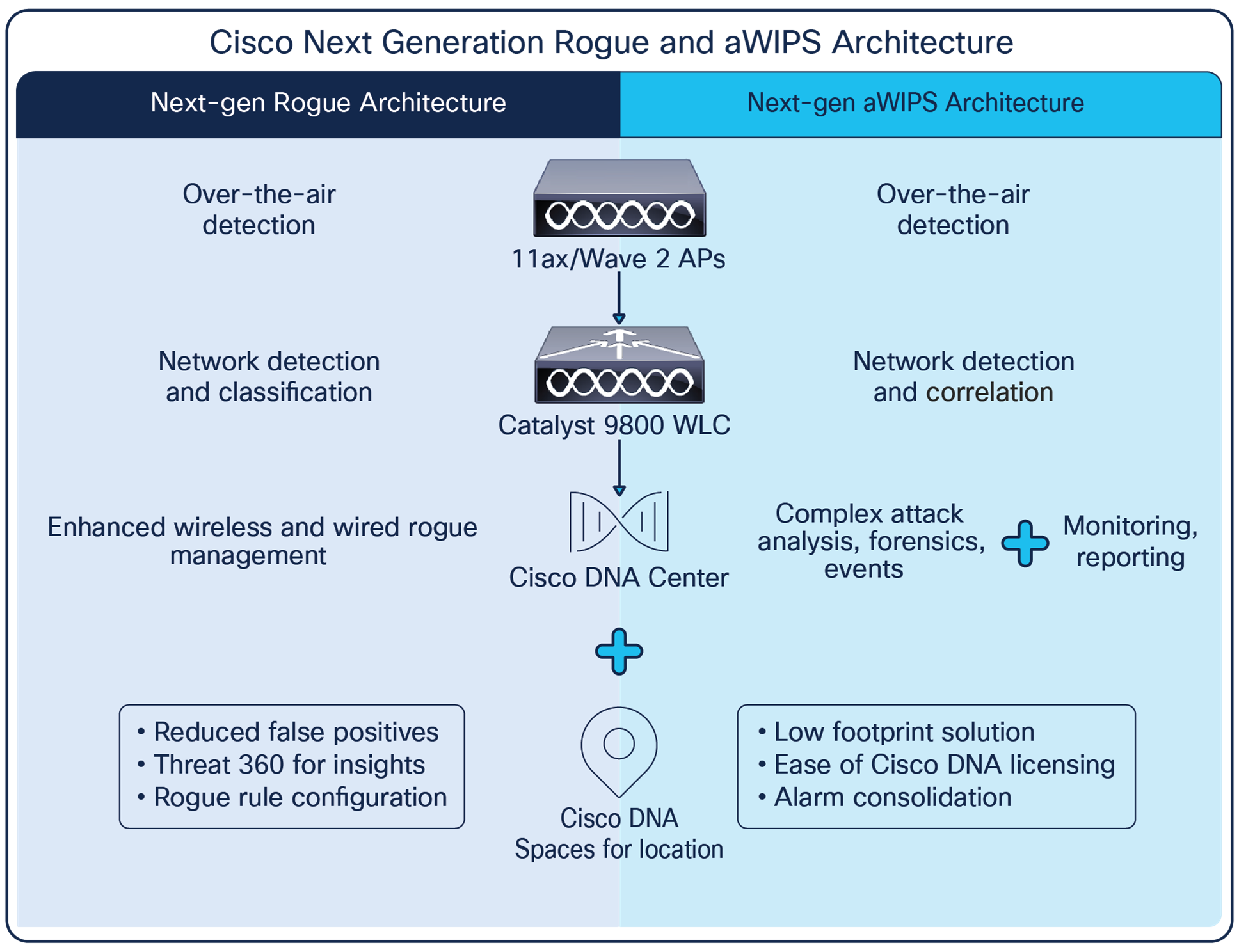
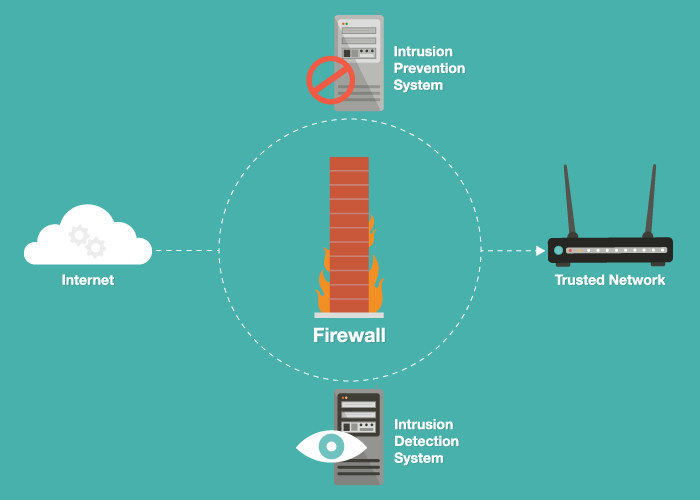
How to detect wireless intrusion. Wireless signals may radiate beyond organizational facilities. Network intrusion detection system (nids): A closer look at wireless intrusion detection aruba white paper introduction as wireless enterprise networks become more pervasive, increasingly sophisticated attacks are developed.
To view the ids window, click more > ids link at the top right corner of the instant main window. They capture data from the radio. Organizations proactively search for unauthorized wireless connections, including the conduct of thorough scans for unauthorized.
One scan cycle is the time it takes an ap radio to complete. View network intrusion detection.docx from cse 145 at kl university. It is the idea that with an additional layer of intelligence,.
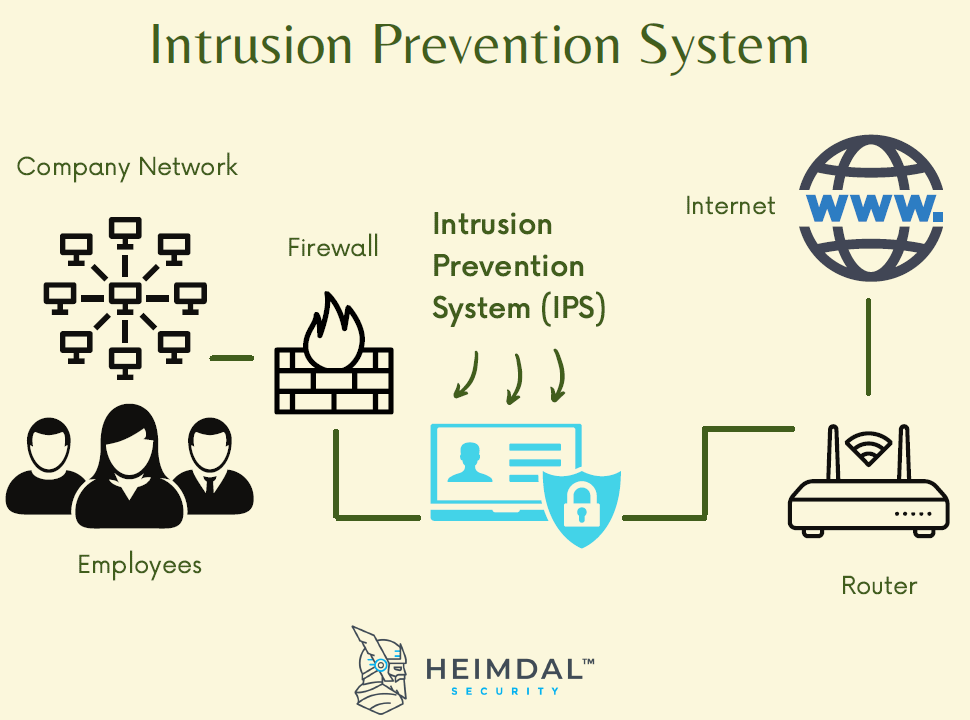
To detect an intrusion, an ap radio scans all the channels in its frequency band of operation, spending 100 ms on each channel. Whenever a visitor opens the trusted website with his specific web browser, the web browser (of the visitor’s client remote machine) will automatically download the webpage. A nids solution is deployed at strategic points within an organization’s network to monitor incoming and outgoing traffic.
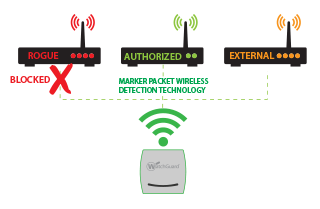
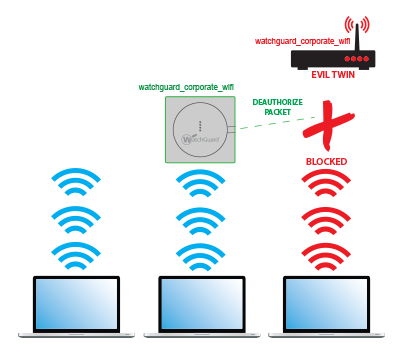
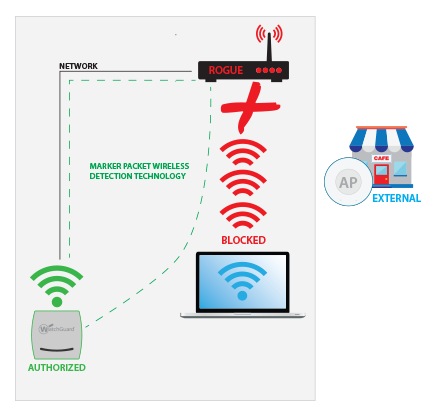
Select configure > wips > automatic intrusion prevention. Numerous federal policies and instructions, such as dodi 8420.01 require that agencies secure and protect their wireless. A wireless intrusion detection system (wids) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools.
Wireless intrusion detection and protection (idp) systems monitor enterprise airwaves with a network of wireless monitors connected to a central server.